
Zero-knowledge proofs (ZKPs) have rapidly become a cornerstone of privacy-preserving technology, particularly within the realm of decentralized identity wallets. These cryptographic protocols allow individuals to demonstrate the validity of a statement, such as confirming their age or residency, without exposing any underlying personal data. In a digital landscape fraught with breaches and escalating surveillance, ZKPs address the critical need for selective disclosure and data minimization.

What Are Zero-Knowledge Proofs and Why Do They Matter?
At their core, zero-knowledge proofs are mathematical methods that enable one party (the prover) to convince another (the verifier) that a certain claim is true, without sharing any additional information. Unlike traditional authentication, which often requires revealing sensitive credentials or documents, ZKPs empower users to prove specific facts about themselves while keeping all other details confidential.
This innovation has far-reaching implications for privacy in digital identity. For example, instead of submitting a full government ID to verify legal drinking age, a user can generate a zero-knowledge proof that simply attests they are over 18, without disclosing their name, birthdate, or address. Such minimal data exposure significantly reduces the risk of identity theft and unauthorized profiling.
The Role of ZKPs in Decentralized Identity Wallets
Decentralized identity wallets, often built on blockchain infrastructure, are designed to give users sovereignty over their digital personas. By integrating ZKPs, these wallets allow individuals and organizations to interact with online services securely and privately. The wallet does not transmit raw credentials; instead, it generates cryptographic attestations tailored to each verification request.
The practical impact is profound. Consider zkLogin, a system leveraging ZKPs for on-chain authentication via familiar platforms like Google or Facebook. With zkLogin, users can authenticate themselves on decentralized applications without revealing actual login credentials or correlating accounts across platforms. This approach shields users from cross-service tracking while maintaining robust security standards.
Selective Disclosure: Minimizing Data Exposure
The principle of selective disclosure lies at the heart of both self-sovereign identity and privacy-centric wallet design. With ZKPs, users can create proofs that reveal only what is strictly necessary for each transaction or interaction. For instance:
- A user proves eligibility for student discounts without exposing their full academic record
- A resident verifies local voting rights without disclosing their home address
- An employee demonstrates compliance with workplace requirements without sharing personal identifiers
This granular control over information sharing represents a paradigm shift from legacy systems, where excessive data collection was the norm, to an architecture where privacy is preserved by default.
The SLVC-DIDA framework exemplifies this shift by employing multi-party authentication through ZKPs rather than traditional public key infrastructures. In such frameworks, no single entity holds all the keys or information required to impersonate a user or compromise their privacy.
ZK Identity Wallets: Empowering Self-Sovereign Identity
ZK identity wallets embody the principles of self-sovereign identity by granting individuals full ownership and management rights over their digital credentials. Through seamless integration with zero-knowledge protocols, these wallets enable trustless interactions across diverse ecosystems, from healthcare and finance to social networks, while ensuring that sensitive attributes remain protected from prying eyes.
This empowerment aligns closely with emerging regulatory expectations around data minimization and user consent. By defaulting to privacy-preserving verification methods like ZKPs, decentralized identity solutions reduce both compliance risk and operational exposure in an increasingly complex threat environment.
Yet, the adoption of zero-knowledge proofs is not without its challenges. Technical complexity, interoperability hurdles, and evolving standards continue to shape the landscape for developers and users alike. Nevertheless, the trajectory is clear: ZKPs are fast becoming a non-negotiable requirement for any digital identity system that values privacy and user agency.
One of the most compelling advantages of ZKPs within decentralized identity wallets is their ability to counteract large-scale data breaches. Because wallets never transmit actual credentials, only mathematical attestations, there is no central honeypot of sensitive information for attackers to target. This architecture drastically reduces the attack surface compared to legacy, centralized databases.
Furthermore, by leveraging ZKPs for on-chain authentication, users can interact with smart contracts and decentralized applications (dApps) without exposing wallet addresses or linking off-chain identities. As a result, even as blockchain ecosystems grow more interconnected, individuals retain granular control over what information they disclose in each context.
Real-World Use Cases of ZKPs in Decentralized Identity Wallets
-

zkLogin by Mysten Labs: zkLogin enables users to authenticate on blockchain platforms using existing credentials (like Google or Facebook) without revealing their actual login details. This preserves privacy while allowing seamless decentralized access.
-

SLVC-DIDA Framework: The SLVC-DIDA system leverages zero-knowledge proofs to provide multi-party authentication in decentralized identity wallets, ensuring users can prove their identity attributes without exposing sensitive data.
-
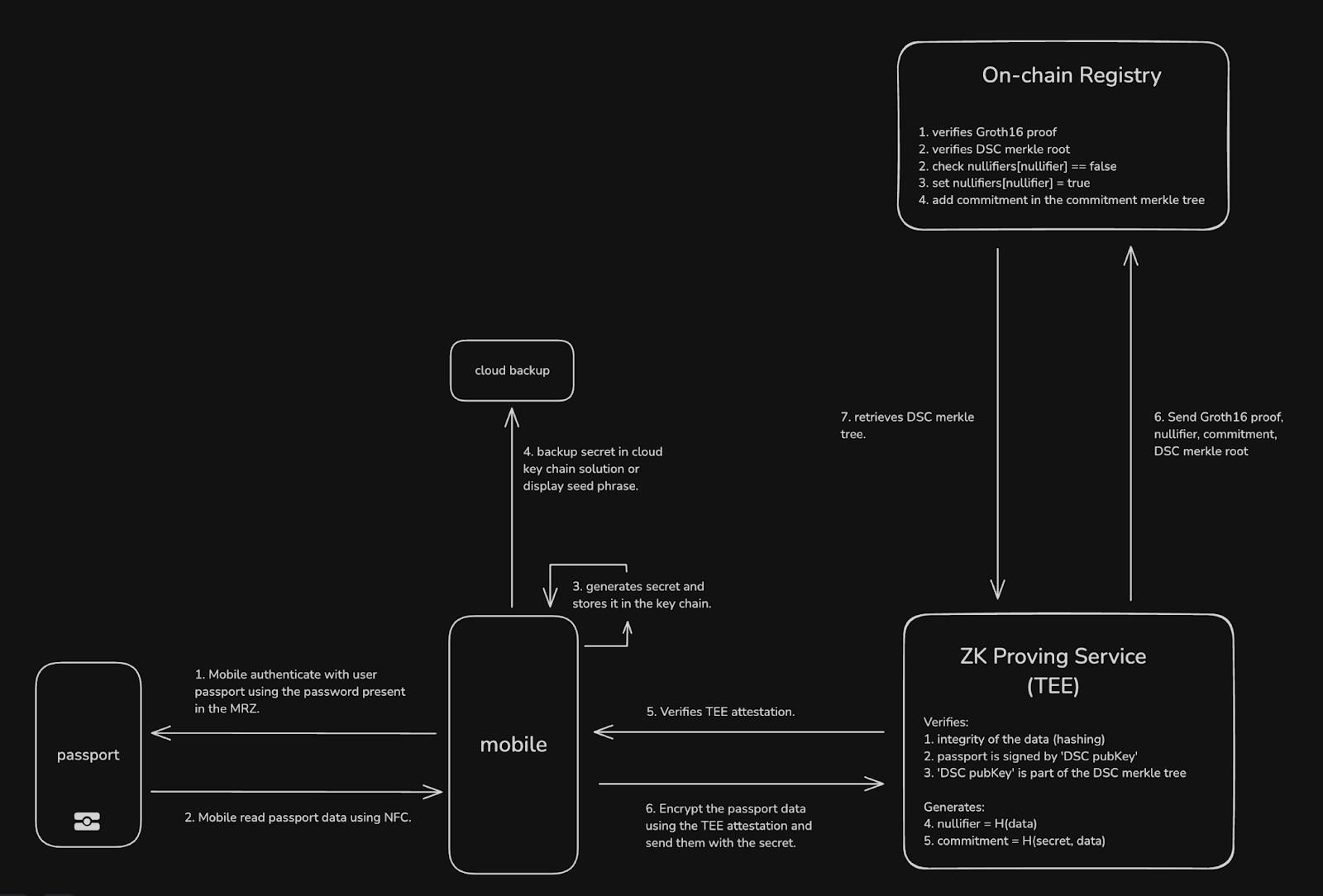
Onchain Passport: Onchain Passport uses ZKPs to let users verify specific attributes (such as age or citizenship) for online services without disclosing full personal information, minimizing data exposure risks.
-
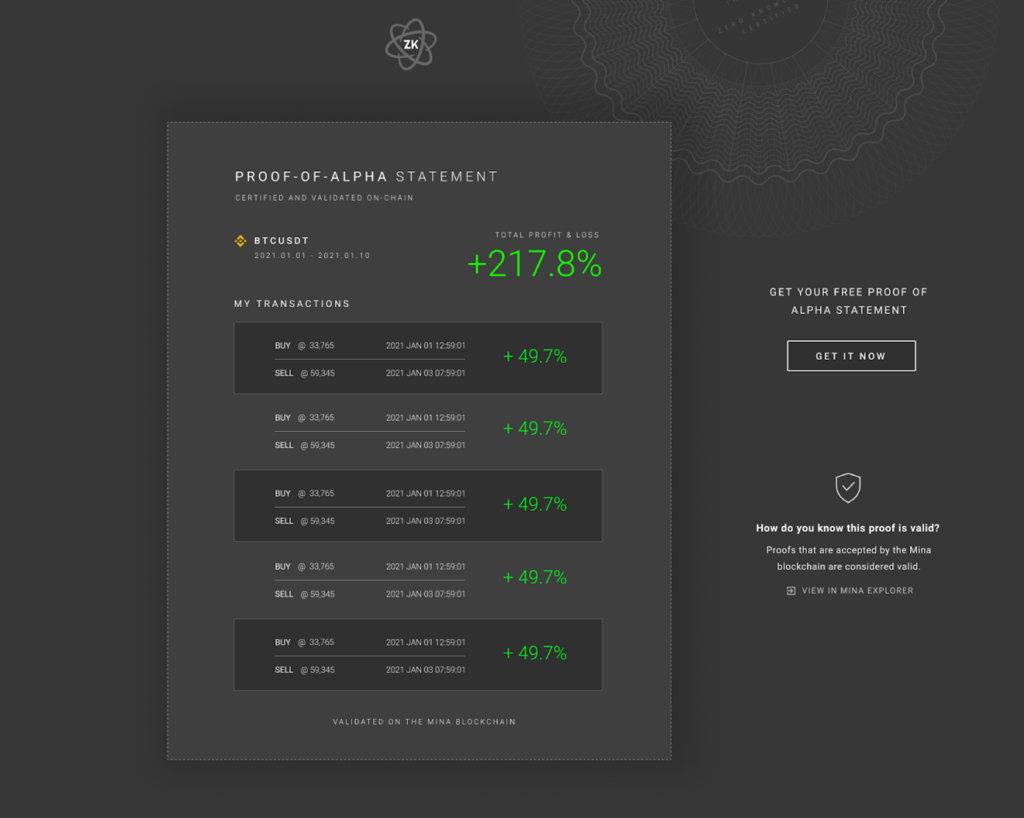
Mina Protocol: Mina Protocol integrates ZKPs for lightweight, privacy-preserving identity verification on its blockchain, allowing users to prove statements about themselves without revealing underlying data.
-
Polygon ID: Polygon ID employs zero-knowledge proofs to enable users to selectively disclose identity credentials for Web3 applications, supporting privacy-first decentralized authentication.
The compliance landscape also benefits from zero-knowledge technology. Regulatory frameworks such as GDPR and emerging digital ID standards increasingly emphasize data minimization. ZKPs allow organizations to meet these requirements while still fulfilling necessary verification functions, whether for age-gated services, anti-money laundering checks, or cross-border onboarding processes.
Current Innovations and Future Outlook
Recent advancements in zk identity wallets have seen integrations with biometric authentication and multi-factor security layers, all while maintaining zero-knowledge guarantees. The SLVC-DIDA framework’s multi-party approach further enhances resilience against single points of failure or collusion among verifiers.
Looking ahead, ongoing research focuses on improving the efficiency and scalability of ZKP protocols so that privacy-preserving verification becomes seamless even at enterprise scale. Projects like zkLogin are already demonstrating how federated credentials can be securely ported into Web3 environments without undermining privacy or usability.
For users and organizations considering a shift toward self-sovereign identity solutions, it is crucial to assess wallet providers’ support for robust zero-knowledge protocols. Not all implementations offer equal levels of privacy assurance; due diligence is required to ensure that selective disclosure and unlinkability are truly enforced at both protocol and application layers.
The promise of privacy in digital identity ultimately rests on empowering individuals, not only with ownership over their credentials but also with practical tools to limit what they share and with whom. By integrating zero-knowledge proofs into decentralized identity wallets, we move closer to a future where trust does not come at the expense of personal data security.
To explore more about how ZKPs are transforming decentralized identity management, and practical guidance for choosing compliant solutions, visit our detailed guide here.






