
Zero-knowledge proofs (ZKPs) have emerged as a transformative technology for privacy-preserving digital identity, fundamentally reshaping how individuals interact with decentralized identity wallets. As the demand for secure and self-sovereign identity management intensifies, ZKPs provide a cryptographically robust solution that enables users to prove assertions about themselves without exposing underlying personal data. This paradigm shift is critical in an era marked by frequent data breaches and growing regulatory scrutiny over digital privacy.

How Zero-Knowledge Proofs Work in Identity Wallets
At their core, zero-knowledge proofs allow one party (the prover) to convince another (the verifier) that a statement is true without disclosing any details beyond the validity of the statement itself. In decentralized identity wallets, this means a user can demonstrate eligibility or possession of credentials, such as age verification or residency, without revealing sensitive information like their full birthdate or address.
This selective disclosure is more than a privacy convenience; it is a security imperative. By minimizing the amount of data exposed during authentication or credential sharing, ZKPs drastically reduce the risk of data leakage and subsequent misuse. For example, instead of sharing an entire government-issued ID to prove majority age, users can simply provide a cryptographic proof that they are over 18 years old, a predicate attestation supported by ZKP protocols (source).
Key Applications: Innovations in Privacy-Preserving DID Wallets
The integration of ZKP decentralized identity mechanisms has driven several innovative use cases within modern digital identity infrastructure:
Key Applications of ZKPs in Decentralized Identity Wallets
-

Selective Disclosure of Attributes: ZKPs enable users to prove specific facts—such as being over 18 years old—without revealing their full birthdate or other sensitive details, minimizing data exposure.
-
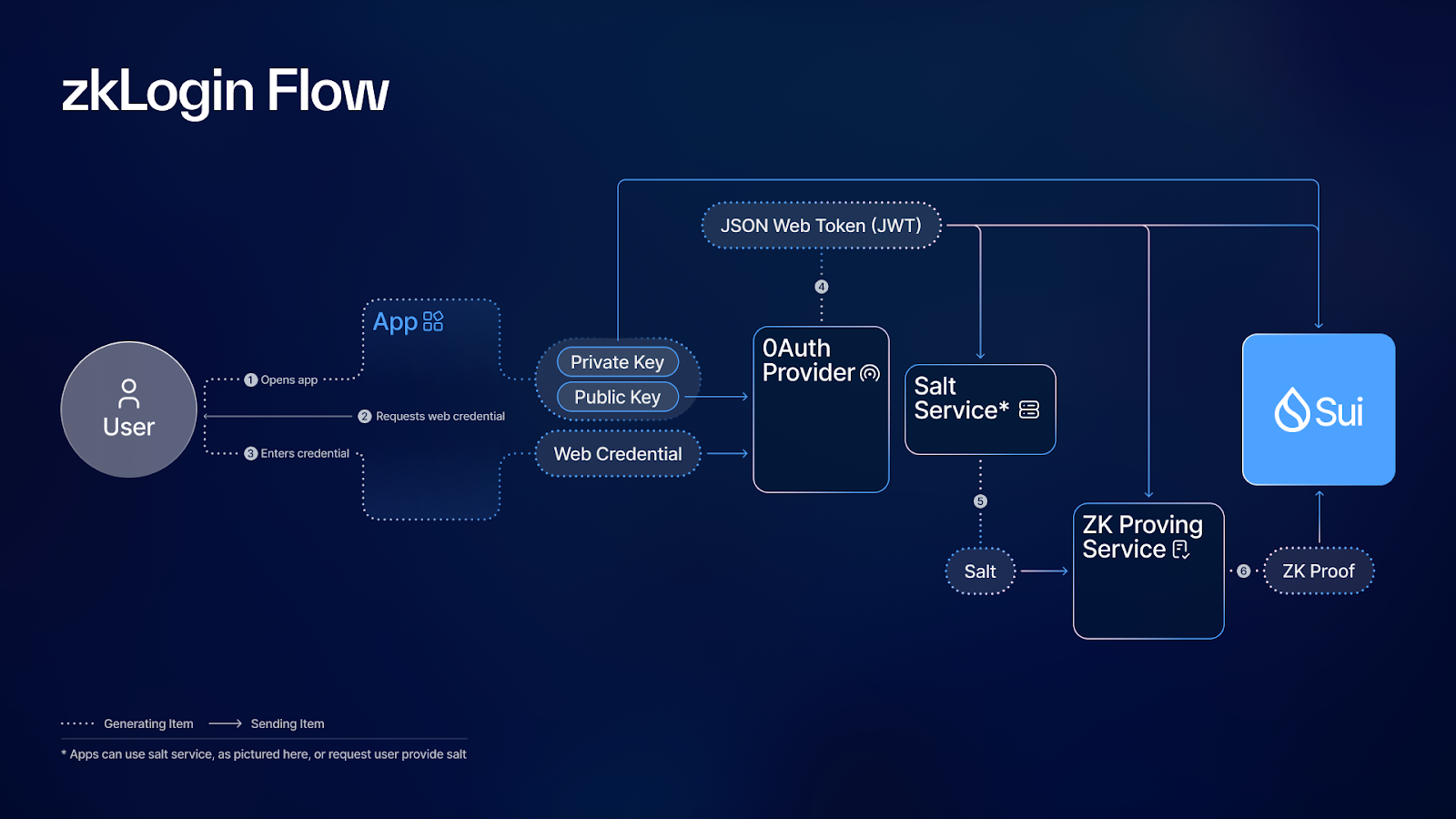
zkLogin Authentication: Solutions like zkLogin use ZKPs to authenticate users via identity tokens (e.g., Google or Facebook) for blockchain transactions, while keeping the link between off-chain and on-chain identities private.
-
Signature-less Verifiable Credentials (SLVC-DIDA): The SLVC-DIDA framework uses ZKPs to issue and verify credentials without relying on traditional signatures or PKI, supporting issuer anonymity and multi-party authentication.
-

zkFaith Protocol for Private Identity Proofs: The zkFaith protocol leverages ZKPs and advanced cryptography to let users prove possession of verified identity data without exposing the data itself, supporting privacy-preserving updates.
-
Decentralized Age and Eligibility Verification: Platforms like Privado ID use ZKPs to let users prove eligibility (such as age or residency) for services without sharing unnecessary personal information.
zkLogin: By leveraging tokens from platforms like Google or Facebook, zkLogin authenticates blockchain transactions while ensuring that the connection between off-chain and on-chain identities remains private, even from the platforms themselves (source). This approach is particularly relevant for onboarding mainstream users into Web3 while maintaining strict privacy guarantees.
SLVC-DIDA: This signature-less verifiable credential framework uses ZKPs to ensure issuer anonymity and enable multi-party authentication without dependence on traditional Public Key Infrastructure (PKI). The result is a truly decentralized ecosystem for credential issuance and verification (source).
zkFaith: Utilizing advanced cryptographic primitives such as aggregated Camenisch-Lysyanskaya signatures and vector commitments, zkFaith allows users to prove possession of verified personal attributes without revealing them. This flexibility supports seamless updates to personal data without reinitiating lengthy verification processes (source).
The Benefits: Data Minimization and User Empowerment
The adoption of privacy-preserving DID wallets, underpinned by ZKP technology, yields tangible benefits for both individuals and organizations:
- Data Minimization: Only essential information is disclosed per transaction, aligning with best practices in GDPR-compliant data handling (source). This reduces attack surfaces and exposure risks.
- User Control: Individuals retain sovereignty over their credentials, deciding what to share, when, and with whom, thereby restoring agency lost in centralized systems.
- Enhanced Security: By withholding sensitive details from verifiers unless strictly necessary, ZKPs significantly lower the risk profile associated with digital interactions.
This shift towards self-sovereign identity using ZKP-based wallets addresses not only technical vulnerabilities but also broader societal concerns around surveillance capitalism and institutional overreach.
Despite the promise of zero-knowledge proofs, practical implementation in decentralized identity wallets is not without challenges. Performance considerations, such as computational overhead and latency, remain a focus for ongoing research and development. As protocols like zkSNARKs and zkSTARKs mature, they are becoming more efficient, but wallet developers must still balance privacy guarantees with user experience. Additionally, interoperability between various DID wallet standards and ZKP protocols is crucial to ensure seamless cross-platform authentication and credential portability.
Risks and Regulatory Considerations in zk Identity Wallet Technology
While zk identity wallet technology offers robust privacy features, it also introduces new risk vectors that must be managed responsibly. Malicious actors could exploit anonymity to bypass compliance checks or perpetrate fraud if verifiable credentials are not rigorously issued or maintained. Wallet providers must implement stringent governance frameworks for credential issuance, revocation, and auditability. Furthermore, as data minimization becomes standard practice through ZKPs, regulatory bodies are reevaluating electronic identification laws to ensure compatibility with privacy-enhancing technologies (source).
Enterprises considering integration of self-sovereign identity ZKP solutions should conduct comprehensive risk assessments, addressing technical vulnerabilities, legal obligations under GDPR or eIDAS frameworks, and the evolving landscape of cross-border data transfer regulations.
The Road Ahead: Adoption and Ecosystem Growth
The adoption curve for privacy-preserving DID wallets powered by zero-knowledge proofs is accelerating as both consumers and institutions recognize the value of minimizing personal data exposure. Projects like Privado ID (built on iden3 protocol) exemplify how open-source collaboration can drive innovation in this space. As more platforms embrace ZKPs for digital identity management, from banking KYC to access control in enterprise applications, the ecosystem will continue to evolve towards greater interoperability and usability.
Market participants should remain vigilant about the pace of technological change while advocating for standards that prioritize individual autonomy and systemic resilience. The convergence of zero-knowledge cryptography with decentralized identifiers is not just a technical milestone, it is a foundational pillar for the future of digital trust.
Best Practices for Implementing ZKPs in Identity Wallets
-

Adopt Proven ZKP Protocols: Utilize well-established zero-knowledge proof frameworks such as zk-SNARKs, zk-STARKs, or the iden3 protocol (as used by Privado ID) to ensure robust privacy and security in credential verification.
-

Enable Selective Disclosure: Implement selective disclosure mechanisms allowing users to prove specific attributes (e.g., age or citizenship) without revealing underlying personal data, following the approach used by Dock Labs and Entrust.
-

Ensure Compliance with Data Minimization Principles: Align ZKP implementations with regulations like GDPR by disclosing only the minimum information necessary, as recommended by Internet Policy Review and practiced in SLVC-DIDA frameworks.
-
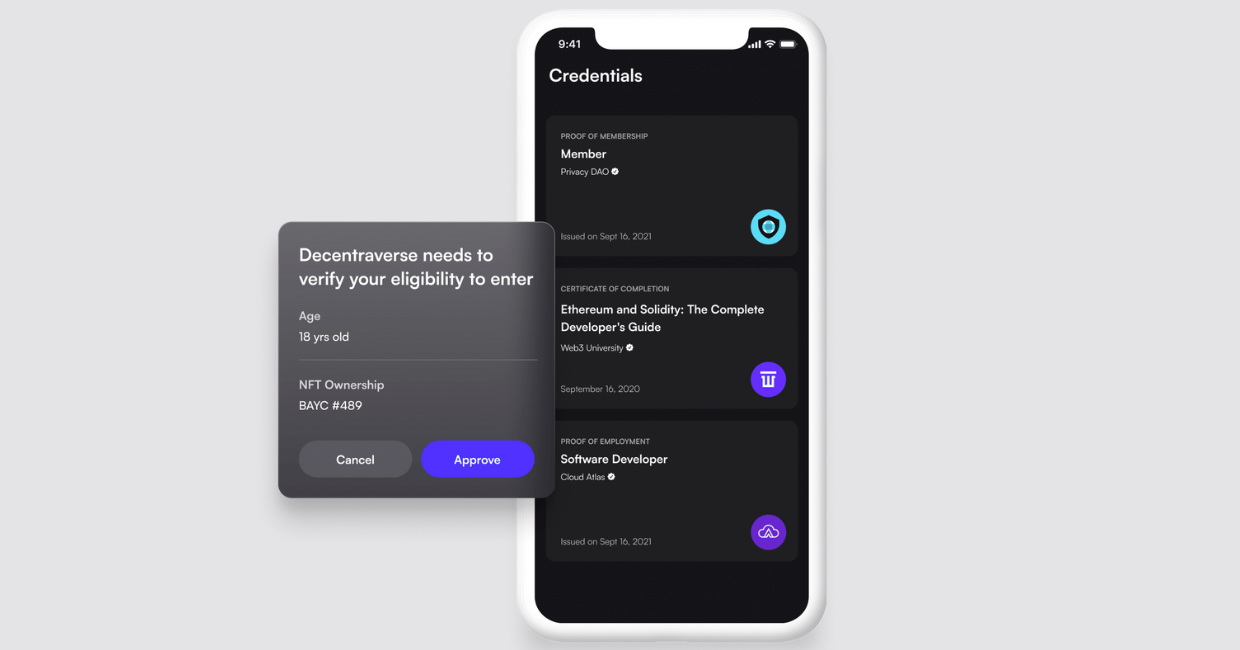
Integrate with Decentralized Credential Standards: Support interoperability by using recognized standards such as W3C Verifiable Credentials combined with ZKP-based privacy enhancements, as seen in platforms like 1Kosmos and Privado ID.
-
Prioritize User Control and Consent: Design wallet interfaces that empower users to manage, approve, and revoke access to their credentials, following the user-centric models of Okta and TokenMinds.
-

Conduct Rigorous Security Audits: Regularly audit ZKP implementations for vulnerabilities, leveraging third-party security experts and open-source community reviews, as practiced by leading projects like zkLogin and zkFaith.
This new paradigm requires a shift in mindset: from trusting centralized authorities with our most sensitive information to embracing cryptographic assurances that empower users directly.






