In 2026, self-sovereign identity has transitioned from niche experimentation to essential infrastructure, driven by zk identity wallets that prioritize user control and privacy. Protocols like zkPass and zkTLS stand out, enabling individuals to verify attributes from Web2 sources without exposing sensitive data. This setup guide explores their integration into zero knowledge identity wallets, offering a practical path for blockchain enthusiasts, developers, and privacy advocates to reclaim digital sovereignty amid tightening regulations.
These tools address a core tension in decentralized systems: proving real-world credentials on-chain without compromising confidentiality. Traditional methods, such as OAuth logins or KYC uploads, centralize trust and invite data breaches. zkPass, a decentralized oracle protocol, counters this by generating zero-knowledge proofs (ZKPs) from HTTPS websites like banks or social platforms. Built on zkTLS, it combines third-party TLS with hybrid ZK techniques, ensuring tamper-proof data retrieval. As of early 2026, zkPass boasts over 2 million attestations across finance, e-commerce, and education, backed by a $12.5 million Series A from investors including dao5 and Animoca Brands.
zkTLS Fundamentals: Securing Web2 Data for DID Wallets
zkTLS redefines secure data composability by embedding ZKPs into the TLS encryption layer, the backbone of HTTPS. This hybrid approach allows provers to attest website content without revealing full payloads or session details. For self-sovereign identity wallets, it means generating DIDs anchored to verifiable claims, such as account balances or course completions, while mitigating replay attacks and oracle centralization risks.
Risk-conscious users must note zkTLS’s reliance on trusted setup phases during proof generation, though ongoing audits and the forthcoming zkPass Node Network aim to decentralize validation. Shoal Research highlights zkTLS’s role in Web2-Web3 interoperability, preventing over-disclosure in regulated environments like finance, where compliance demands proof without raw data handover.
zkPass Ecosystem: Empowering Privacy-Preserving DIDs
zkPass elevates zkPass DID capabilities, transforming private internet data into on-chain verifiables. Users prove legal identity, financial records, or healthcare info via mobile-optimized flows, sidestepping file uploads. The 2026 roadmap accelerates this with zkTLS upgrades for faster proving, SDK v2.0 for unified web-mobile support, and community nodes to scale beyond team-operated setups.
Compared to rivals, zkPass excels in breadth: attestations span global institutions without API silos. Developers integrate via SDKs, issuing privacy preserving DID wallets that selective-disclose attributes. Yet, adoption hinges on prover efficiency; current latencies suit batch verifications but demand optimization for real-time DeFi KYC.
zkTLS vs Traditional Identity Methods
| Method | Privacy Level | Data Exposure | Setup Complexity | Use Cases |
|---|---|---|---|---|
| zkTLS | High (ZKPs) ✅ | Minimal (proof only) ✅ | Medium (SDK install) | SS Identity, Regulated Finance |
| OAuth | Low ❌ | Full session data ❌ | Low | Social logins |
| Manual KYC | None ❌ | All documents ❌ | High | Banks, Exchanges |
Essential Prerequisites for zkPass and zkTLS Deployment
Before diving into zkTLS decentralized identity setup, secure a robust environment. Begin with a hardware wallet or MetaMask for DID management, ensuring EVM-compatible chains like Ethereum or Polygon. Install Node. js v20 and and Rust toolchain for proof compilation; zkPass docs recommend 16GB RAM minimum to handle circuit generation.
Register at zkPass dashboard for API keys, vital for initial attestations. Verify browser extensions like the zkPass prover plugin, compatible with Chrome and Firefox. For developers, clone the zkPass GitHub repo and run npm install to bootstrap. Risk assessment: audit dependencies for supply-chain vulnerabilities, as ZK libraries evolve rapidly. Test on testnets to simulate production loads, confirming proof validity before mainnet commits.
Next steps involve configuring zkTLS sessions, but first, familiarize with credential schemas via official user guides. This foundation minimizes errors in proof issuance, crucial for self-sovereign control.
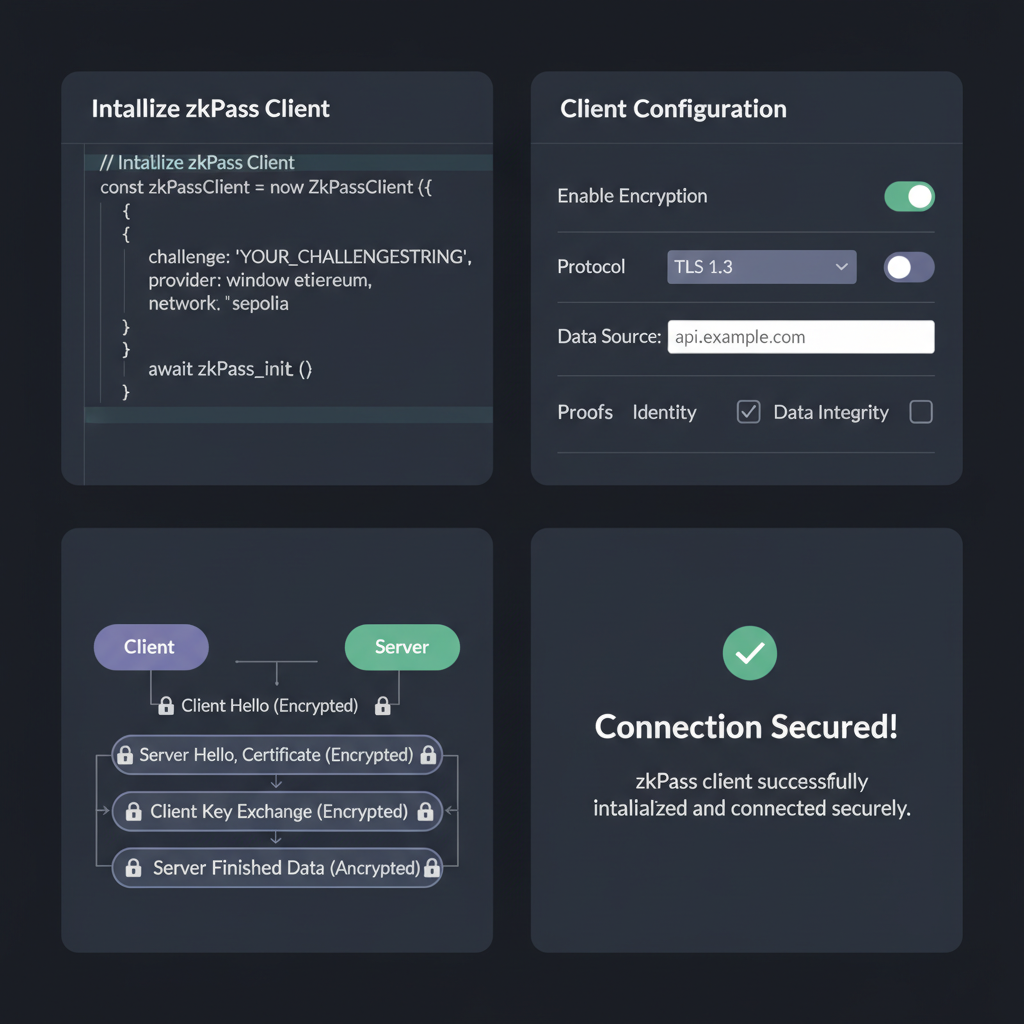
Configuring zkTLS sessions starts with selecting target HTTPS endpoints, such as your bank portal or LinkedIn profile. Access the zkPass dashboard, input the URL, and initiate a prover session via the browser extension. This captures the TLS handshake and page content into a verifiable circuit, outputting a ZKP without storing raw data. Developers script this via SDK, binding proofs to DIDs for wallet storage.
Step-by-Step zkPass Setup: From Prover to Self-Sovereign Wallet
Once prerequisites align, launch the zkPass CLI with zkpass prover init, specifying schema for attributes like “account-balance-gt-1000”. Compile the circuit using Rust-based tools, a process demanding patience as initial runs clock 5-10 minutes on standard hardware. Verify the proof locally against a mock verifier before on-chain submission. This workflow empowers zero knowledge identity wallets, where users issue Verifiable Credentials (VCs) compliant with W3C standards, revokable via DID document updates.
Institutional adopters, draw from my fixed income background: treat zkTLS proofs as collateral-grade attestations. They satisfy Basel III-like requirements for AML without PII leakage, a boon amid MiCA and evolving U. S. regs. Yet, latency remains a friction point; Q1 2026’s protocol upgrade promises sub-second proves on mobiles, critical for DeFi lending protocols demanding instant KYC.
Generating and Verifying zkTLS Financial Proofs with zkPass SDK
The following JavaScript example demonstrates the use of the zkPass SDK to generate and verify a zkTLS proof for a financial credential within a self-sovereign DID wallet. This enables privacy-preserving attestation of financial attributes, such as account balance ranges, without disclosing full details. Prerequisites include installing the zkPass SDK (`npm install @zkpass/sdk`) and configuring secure API credentials.
// Example using zkPass SDK for zkTLS proof generation and verification in a self-sovereign DID wallet
import { ZkPassClient } from '@zkpass/sdk'; // Install via: npm install @zkpass/sdk
async function handleFinancialZkTLSProof(walletDID) {
try {
// Initialize zkPass client - secure API keys in production
const zkPass = new ZkPassClient({
appId: process.env.ZKPASS_APP_ID, // Use environment variables
serverUrl: 'https://api.zkpass.org'
});
// Define zkTLS query for financial credential
// WARNING: Use only trusted financial institution URLs to mitigate phishing risks
const query = {
type: 'zkTLS',
url: 'https://bank.example.com/dashboard', // Replace with actual bank URL
credentialTemplate: 'financial-account',
selectors: {
balance: '#account-balance',
accountType: '.account-type'
},
circuitParams: {
revealBalanceRange: 'balance > 1000 && balance < 100000', // Privacy-preserving reveal
hideAccountDetails: true
}
};
// Generate proof (requires user browser interaction with site)
const proof = await zkPass.generateProof(query);
// Verify proof locally or on server
const isValid = await zkPass.verifyProof(proof);
if (isValid) {
// Store as verifiable credential in DID wallet
const vc = {
'@context': ['https://www.w3.org/2018/credentials'],
type: ['VerifiableCredential', 'FinancialProof'],
credentialSubject: {
id: walletDID,
proofData: proof.publicSignals
},
proof: proof.proof
};
console.log('Financial zkTLS VC generated:', vc);
// Persist to wallet storage
return vc;
} else {
throw new Error('Proof verification failed');
}
} catch (error) {
console.error('zkTLS proof error:', error);
// Risk mitigation: Log without exposing sensitive data
throw error;
}
}
// Usage example:
// handleFinancialZkTLSProof('did:example:wallet123');**Security and Risk Considerations:** This code is illustrative and not production-ready. zkTLS proofs rely on TLS session integrity; users must verify site authenticity to prevent man-in-the-middle attacks. Always perform server-side verification, implement rate limiting, and conduct third-party audits. Compliance with financial regulations (e.g., PSD2, KYC/AML) is mandatory. Handle errors gracefully to avoid leaking sensitive data, and store proofs securely in the DID wallet.
Integrating zkPass Proofs into DID Wallets: Practical Deployment Risks and Mitigations
Link zkPass outputs to wallets like Argent or Safe via ERC-725Y proxies, storing proofs as soulbound tokens or off-chain references hashed on-chain. Use Semaphore or Reclaim protocols for zero-knowledge aggregation, compounding proofs into composite claims, say "over-18 AND university-graduated". This selective disclosure fortifies privacy preserving DID wallets against correlation attacks.
Risks demand scrutiny. Prover centralization pre-Node Network rollout risks single points of failure; mitigate by batching attestations and cross-verifying with multiple oracles. Quantum threats loom over TLS assumptions, though hybrid ZK layers add post-quantum resilience. Audit trails reveal zkPass's clean record post-Series A, but always simulate adversarial fetches. For enterprises, governance via multisig DID controllers prevents key loss, echoing traditional market infrastructure safeguards.
Real-world pilots underscore viability: financial firms leverage zkPass for income proofs in undercollateralized loans, slashing default rates by anonymizing borrower profiles. Education platforms issue degree VCs, verifiable sans transcripts. As the zkPass Node Network decentralizes in 2026, expect explosive growth, positioning zk identity wallets as the default for regulated Web3.
Mastering zkPass and zkTLS equips you to navigate identity's frontier, balancing sovereignty with verifiability. Experiment on testnets, contribute to node operations, and audit your setups rigorously. This tech stack not only future-proofs personal data but rearchitects trust in decentralized markets.