As digital identity becomes foundational to online interaction, the limitations of traditional biometrics are increasingly apparent. While fingerprint and facial recognition have made verification more convenient, they often require users to surrender sensitive biological data to centralized entities. With privacy concerns and regulatory scrutiny on the rise, a new paradigm is emerging: mobile-first decentralized identity wallets that move beyond biometrics, leveraging cryptographic proofs and verifiable credentials for secure, user-centric verification.

The Shift Toward Mobile-First Human Verification
The ubiquity of smartphones has catalyzed a revolution in how individuals manage and prove their identities. Modern mobile decentralized identity wallets empower users to store, manage, and share digital credentials – such as government IDs or proof-of-uniqueness – directly from their devices. This approach not only improves accessibility but also puts control squarely in the hands of the user.
For example, Identity.com’s mobile app enables users to add verifiable credentials (VCs) for age verification or KYC processes without exposing unnecessary personal data. Credentials are cryptographically signed and can be presented on demand, reducing reliance on passwords or centralized databases vulnerable to breaches.
Beyond Biometrics: Cryptographic Proofs and Privacy by Design
The next generation of human verification is defined by privacy-preserving cryptographic techniques. Instead of sharing biometric data with third parties, users can generate zero-knowledge proofs (ZKPs) that attest to certain facts (such as being over 18) without revealing underlying information. This shift is not just theoretical; it’s already being implemented in solutions like Humanity Protocol’s palm scan system, which uses one-way encrypted vectors for authentication rather than storing raw images or templates.
This approach aligns with global standards such as those set by the W3C for decentralized identifiers (DIDs). DIDs enable persistent identification without centralized registries, supporting self-sovereign identity models where individuals retain full ownership over their digital presence.
Key Advantages of Mobile-First Human Verification
-
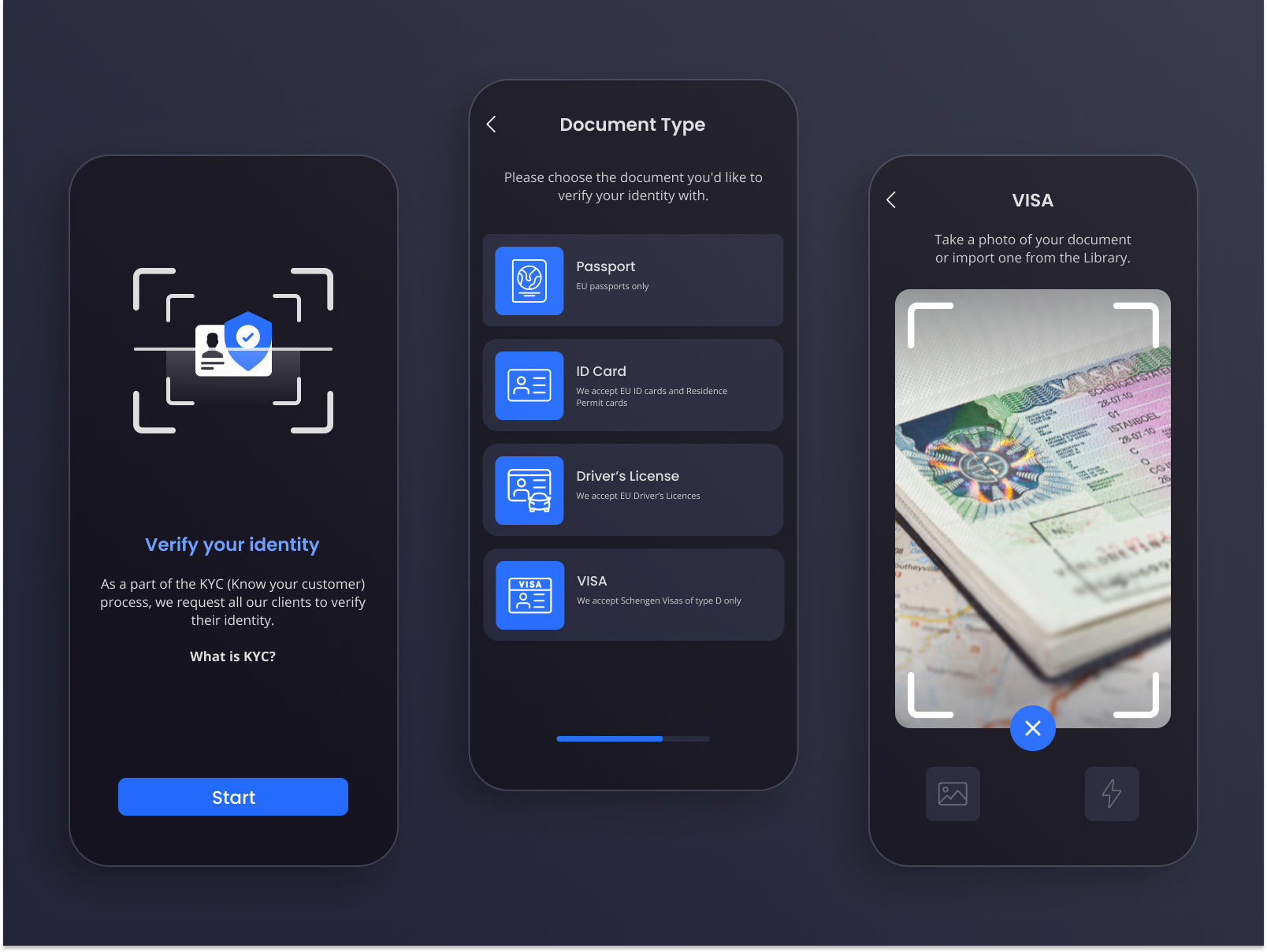
User-Centric Control: Mobile-first decentralized identity solutions, such as Identity.com, empower individuals to manage and share their digital credentials directly from their smartphones, giving users full control over their personal data.
-
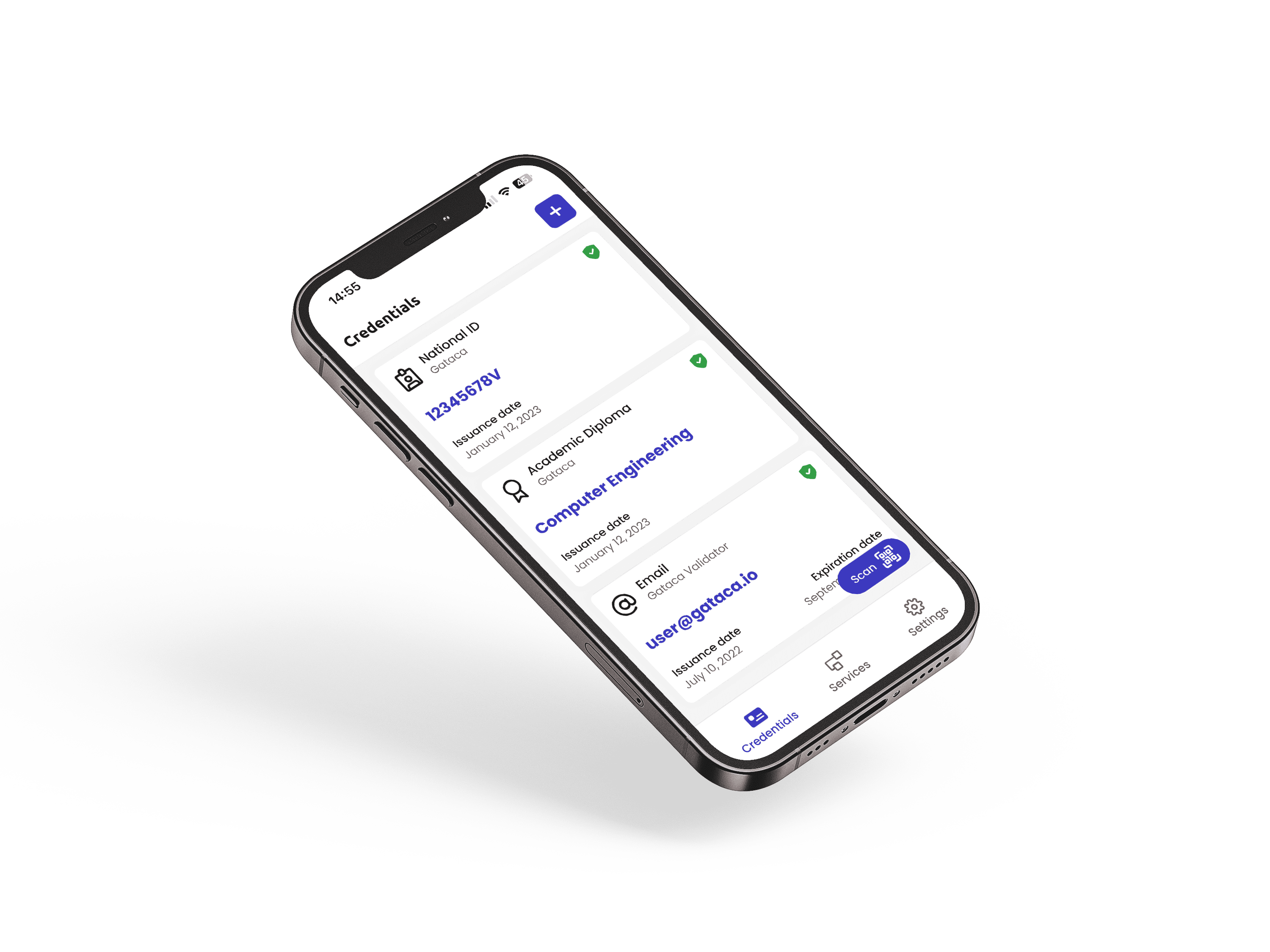
Interoperability and Compliance: Solutions such as Gataca and Veridas Nexus support verifiable credentials and adhere to global standards like those set by the W3C, ensuring compatibility across diverse platforms and regulatory environments.
-
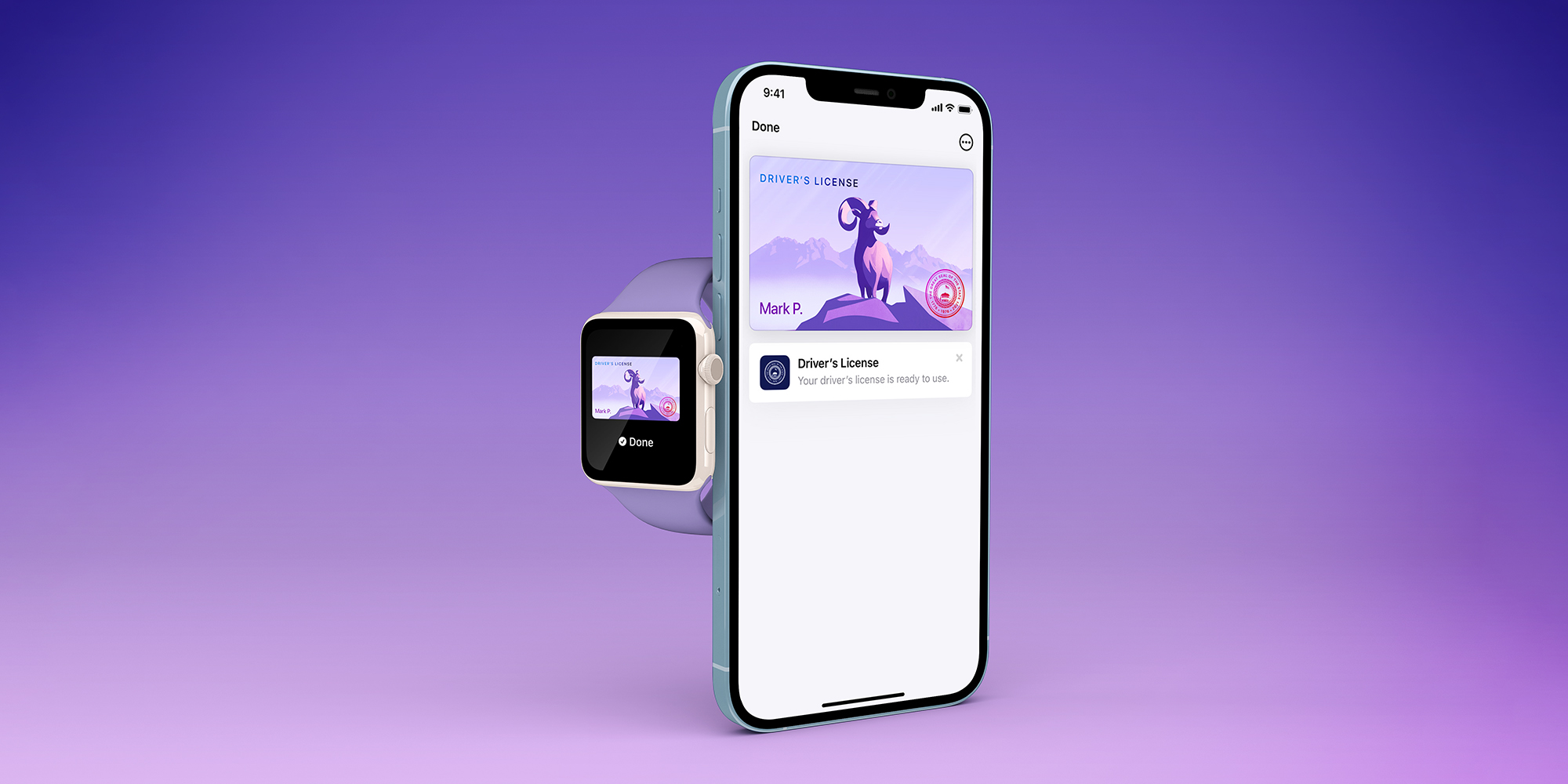
Streamlined User Experience: Mobile-first verification allows for quick, passwordless authentication and seamless onboarding, as seen with Apple Wallet’s digital ID and 1Kosmos reusable identity wallets, reducing friction for both users and organizations.
-

Scalability and Accessibility: The widespread adoption of smartphones enables decentralized identity systems like Humanity Protocol to reach millions globally, making secure human verification accessible to a broader population without specialized hardware.
Global Momentum: Real-World Deployments and Standards
Adoption isn’t limited to startups or pilot projects. National-level initiatives like China’s RealDID system demonstrate how blockchain-based DIDs can deliver real-name verification while preserving anonymity for millions of citizens accessing online services. Meanwhile, platforms such as Veridas Nexus and Gataca are equipping organizations worldwide with tools to issue and verify digital credentials securely, ushering in an era where biometric-free verification becomes the norm rather than the exception.
The convergence of reusable ID wallets (as seen with 1Kosmos), passwordless authentication protocols like FIDO CTAP supported by Apple Wallet in iOS 26, and privacy-first protocols such as World ID signals rapid maturation in this sector. These solutions address both regulatory compliance needs and end-user demands for autonomy and confidentiality.
What sets these mobile decentralized identity wallets apart is their ability to deliver frictionless, privacy-centric verification at scale. By combining cryptographic proofs with intuitive mobile interfaces, users can prove their humanity or eligibility for services without ever relinquishing sensitive biometric data or personal identifiers. This approach not only reduces the attack surface for fraud and identity theft but also aligns with emerging data protection regulations worldwide.
“The future of digital identity is about giving control back to the user, biometric-free verification powered by cryptography and mobile-first design is a leap in that direction. ”
How Mobile-First Human Verification Works in Practice
Modern solutions like Identity.com’s app and Humanity Protocol’s palm scan system illustrate practical deployments. Identity. com empowers users to store multiple verifiable credentials (VCs), which can be selectively disclosed for KYC, age checks, or proof-of-uniqueness scenarios. Each credential is cryptographically signed, ensuring authenticity while letting users remain anonymous where appropriate.
Humanity Protocol’s adoption of palm vein scans goes a step further by transforming raw biometric input into encrypted feature vectors using advanced homomorphic encryption. This method ensures that even if authentication data is intercepted or compromised, no usable biometric information can be extracted, an essential advance in privacy-preserving design.
Key Features Powering the Next Generation of Digital ID Wallets
Key Features of Top Cryptographic Identity Wallets (2025)
-

Mobile-First Credential Management: Leading wallets like Identity.com and Wultra Digital ID Wallet provide intuitive mobile apps for storing, sharing, and managing verifiable credentials (VCs) directly from smartphones, ensuring accessibility and convenience.
-
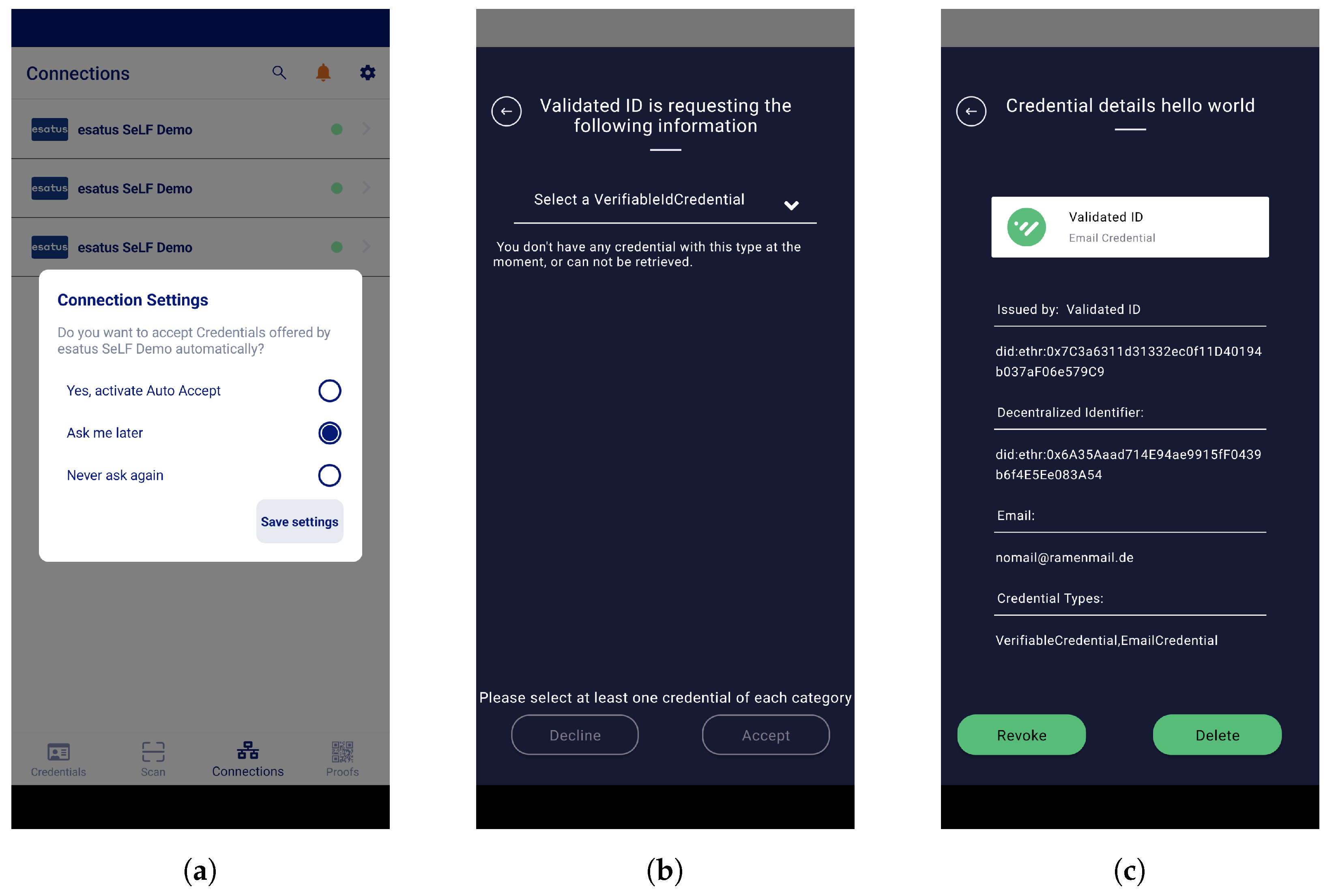
Self-Sovereign Identity (SSI) Support: Solutions such as Gataca and Veridas Nexus empower users with full control over their digital identities, enabling them to issue, present, and revoke credentials without relying on centralized authorities.
-

Privacy-Preserving Biometrics: Platforms like Humanity Protocol and Daon integrate advanced biometrics—such as palm vein scans and encrypted facial recognition—while leveraging privacy-enhancing technologies like homomorphic encryption to protect sensitive data.
-
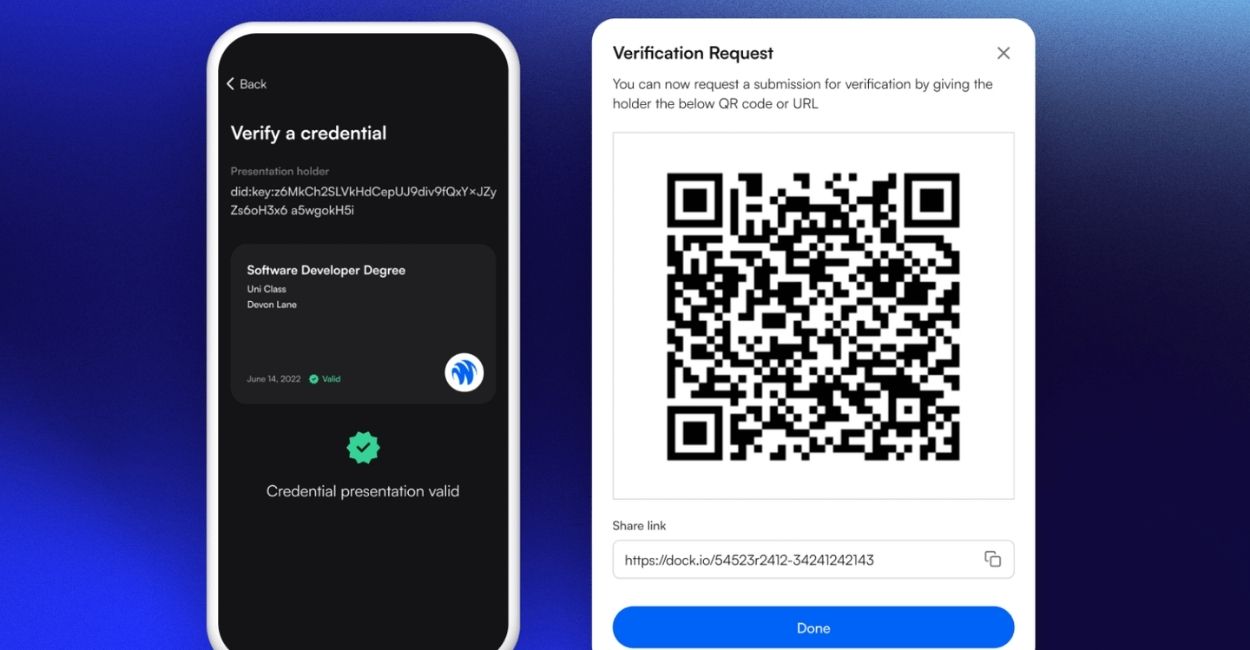
Verifiable Credential Interoperability: Adherence to W3C Decentralized Identifier (DID) and Verifiable Credentials standards ensures that wallets like Dock Labs and 1Kosmos can issue and accept credentials across multiple platforms and jurisdictions.
-

Regulatory Compliance and KYC Integration: Many wallets, including Keyless and Identity.com, streamline Know Your Customer (KYC) processes for businesses, offering compliant onboarding and verification while preserving user privacy.
-

Decentralized and National-Scale Deployments: Large-scale systems like China RealDID demonstrate the viability of blockchain-based, decentralized identity at a national level, enabling secure, pseudonymous access to government and online services.
The introduction of reusable digital ID wallets by platforms like 1Kosmos and Dock Labs means individuals can now access everything from government IDs to social security cards through a single secure interface. Passwordless authentication protocols such as FIDO CTAP are increasingly integrated into mainstream devices, enabling Face ID or Touch ID logins without storing passwords on centralized servers.
PrivadoID, World ID, and similar protocols are pushing boundaries further by prioritizing zero-knowledge technology at the core of their architecture. These systems allow organizations to verify attributes (like liveness or uniqueness) without collecting any unnecessary user data, a crucial leap forward for both compliance and user trust.
Looking Ahead: The Road to Universal Biometric-Free Verification
The momentum behind biometric-free verification is unmistakable. As more jurisdictions adopt digital credentials and organizations embrace decentralized architectures, interoperability between wallets and credential issuers will become paramount. Standards set by W3C DIDs and verifiable credentials are already smoothing this path, allowing seamless integration across platforms and borders.
The ultimate promise? A world where proving your humanity or eligibility online becomes as simple as tapping your phone, no passwords, no invasive scans, no third-party surveillance. Instead, you hold your digital keys and decide exactly what to share and when.
Would you trust a cryptographic identity wallet more than traditional biometrics for verifying your identity online?
With the rise of mobile-first decentralized identity solutions, users can now manage digital credentials securely from their smartphones. These wallets use cryptography for privacy and control, while biometrics like palm scans and Face ID remain widely used. Which approach do you trust more for online identity verification?
This shift isn’t just about technology; it’s about restoring agency over digital lives in an era defined by surveillance capitalism and relentless data breaches. As mobile-first decentralized identity continues its rapid evolution, expect to see even greater emphasis on privacy-by-design principles, and a new generation of users empowered to move beyond biometrics entirely.